3 minutes
The 2026 Deep Dive
Going Deeper into Code Review, Reverse Engineering, and Web Exploitation
New year, new focus. This year I’m pushing myself to level up in three specific areas: code review, reverse engineering, and web exploitation. I’ve spent enough time doing surface-level testing, now I want to understand what’s actually happening under the hood. I’ve already invested in the learning materials to make this happen, so there’s no backing out now.
The Reading List
First up is Eugene Lim’s “From Day Zero to Zero Day.” This book covers exactly what I need; code review, reverse engineering, and fuzzing. It’s rare to find one resource that hits all three topics I’m targeting, so this felt like the perfect starting point.

The Course Lineup
I picked up four courses from Cyberwarfare Labs that align with where I want to go:
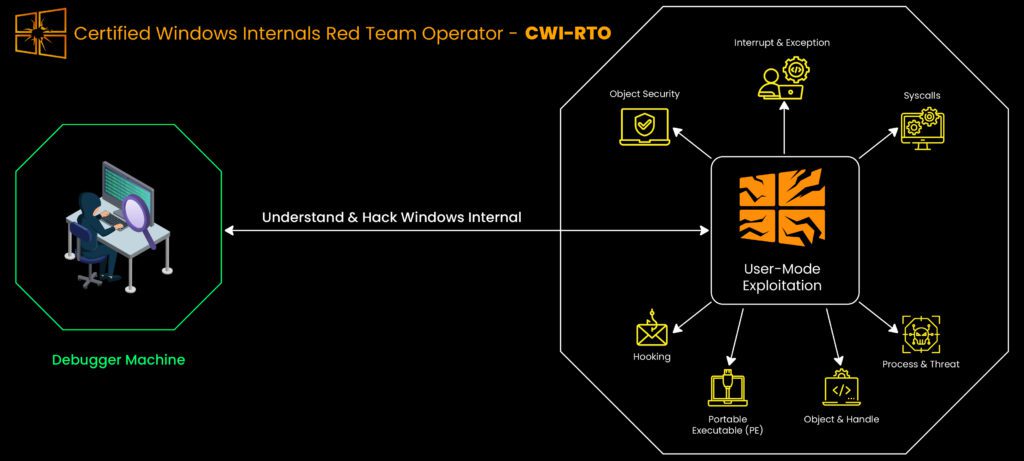
Certified Windows Internals Red Team Operator (CWI-RTO) – I’m already working through this one. It’s teaching me about Windows internals, Win32 and NT APIs (the ones malware loves to abuse), user-mode malware analysis, and kernel data structures using WinDbg. Understanding EPROCESS, ETHREAD, and KPCR has been eye-opening so far.
Certified Exploit Development Professional (CEDP) – This is where I’ll get my hands dirty with exploit development. The focus is on stack exploitation techniques, which I’ve dabbled in before but never properly mastered.

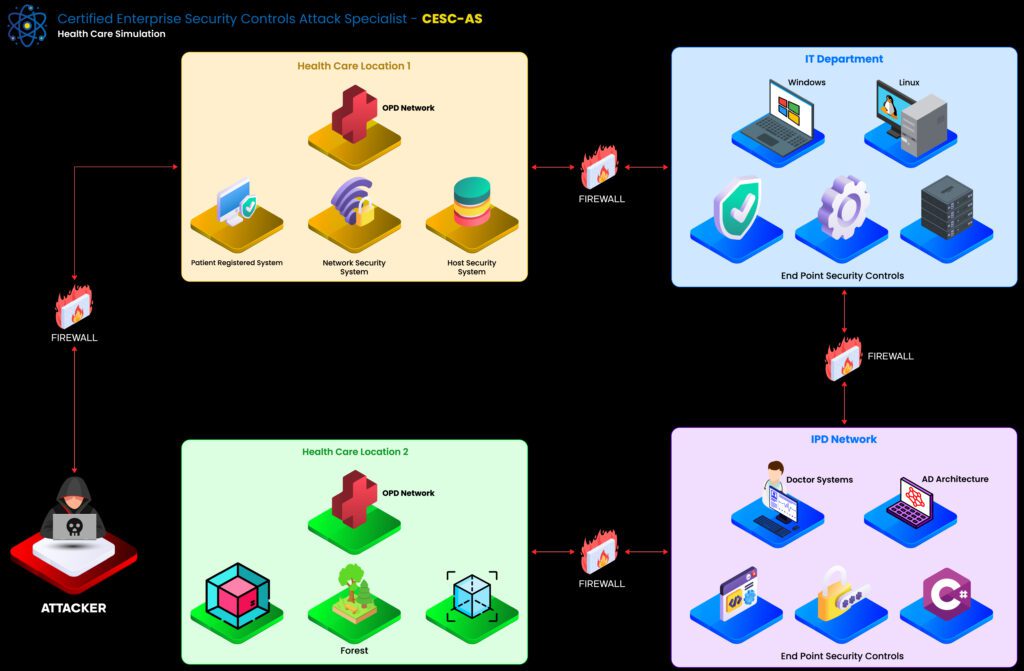
Certified Enterprise Security Controls Attack Specialist (CESC-AS) – I grabbed this during Black Friday when the price dropped significantly. It covers advanced penetration testing, offensive C# tradecraft, Windows API abuse, and deeper Active Directory attacks. Honestly, the discount made it impossible to pass up.
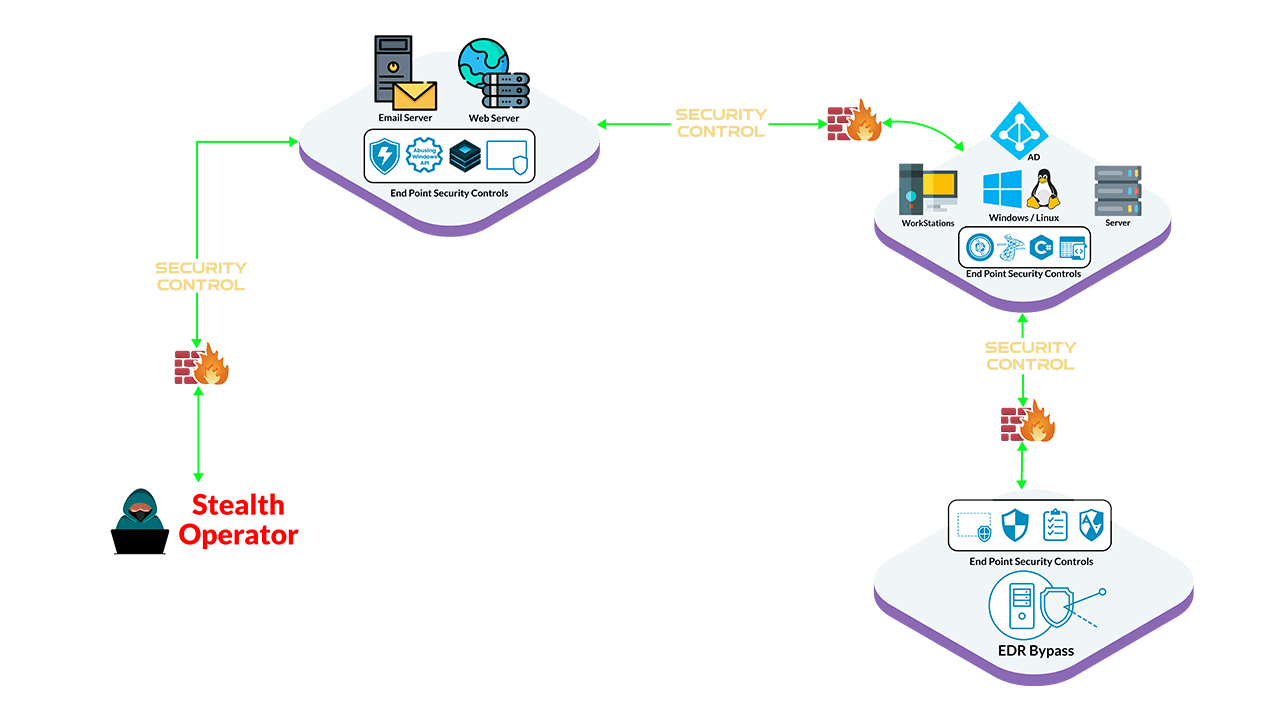
Certified Stealth Cyber Operator (CSCO) – The final boss. Also a Black Friday purchase. This one is packed: red team infrastructure setup, abusing misconfigured security controls, offensive tradecraft development using C, C++, and C#, and techniques for bypassing endpoint security like AV and EDR. It’s ambitious, but that’s the point.
Web Exploitation To round things out, I’m planning to tackle the HTB Certified Web Exploitation Expert (HTB CWEE). This will push my web exploitation skills further with advanced injection attacks, NoSQL injection, XSS and CSRF exploitation, whitebox testing, and more.

The Reality Check
Looking at this list, I know it’s a lot. I’m not expecting to finish everything in one year, but having a clear roadmap helps. The goal isn’t just to collect more certifications, it’s to genuinely understand these topics at a deeper level and apply them in real scenarios.
I’ll be documenting what I learn along the way, sharing the challenges I hit, and posting walkthroughs when things click. If you’re working on similar goals or have advice on any of these topics, I’d love to hear from you.
Let’s see where 2026 takes us.