6 minutes
Certified Cyber Security Engineer [CCSE] Review: Is it Worth it?

I recently completed the Certified Cyber Security Engineer (CCSE) certification from Cyberwarfare Labs, and I wanted to share my experience with anyone considering this certification. Even though I already hold more advanced certifications like the OSCP and HackTheBox CPTS, I found the CCSE to be a valuable addition to my skill set, and here’s why.
What is the CCSE?
The Certified Cyber Security Engineer (CCSE) is a comprehensive penetration testing certification offered by Cyberwarfare Labs. What makes it stand out is its broad coverage of modern attack surfaces that many traditional pentesting certifications don’t touch. It’s designed for beginner to intermediate cybersecurity professionals who want to develop a well-rounded understanding of various technologies and attack vectors they’ll encounter as a cybersecurity engineer.
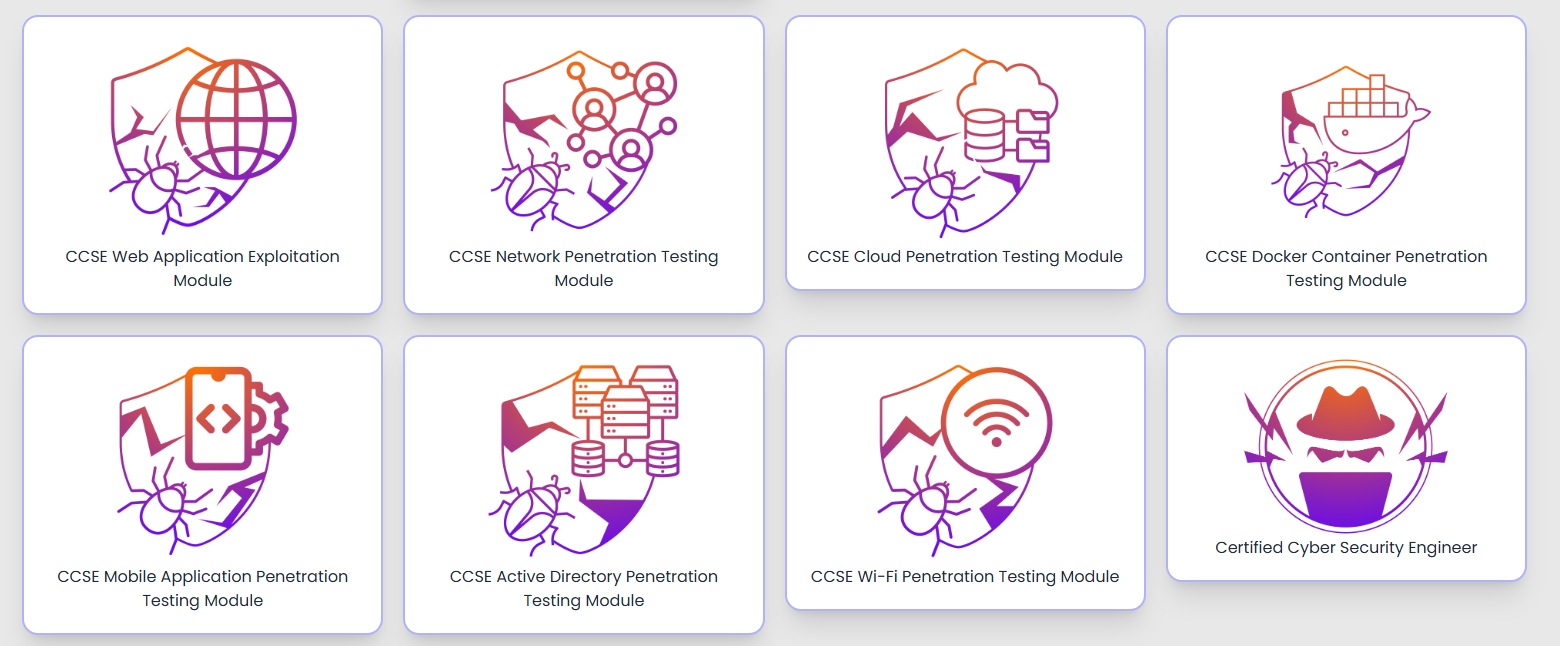
Course Content: 14 Modules of Comprehensive Coverage
The CCSE breaks down into 14 modules that cover everything from fundamentals to specialized topics:

What really sets this course apart is its coverage of cloud penetration testing, Docker container exploitation, mobile application testing, and Wi-Fi security. These are areas that neither the OSCP nor the CPTS covered when I took them, making the CCSE a valuable complement to those certifications.
While the course doesn’t go extremely deep into these specialized topics, it provides enough foundational knowledge to get you started. I think this was intentional, especially since Cyberwarfare Labs offers more advanced certifications focused specifically on cloud penetration testing. For a certification targeting beginner to intermediate professionals, this breadth makes perfect sense, as a cybersecurity engineer, you need exposure to a wide range of technologies.
The Learning Experience
Lab Environment
The lab environment was fantastic. I experienced zero downtime or issues throughout my entire learning period, which is more than I can say for some other certification labs I’ve used.

The labs come in two formats:
VM-Based Labs: These are for modules that require local setup on your own machine, including scripting/programming, OSINT, phishing, exploit development, cloud pentesting, Docker pentesting, mobile pentesting, and Wi-Fi pentesting. The great thing about this approach is that you can experiment freely, break things, and test additional techniques you’ve researched without worrying about affecting a shared environment.
My favorite was the Wi-Fi penetration testing module. Wi-Fi testing typically requires specific hardware and setup to put your network interface in monitoring mode and capture packets. Here, you’re provided with a complete simulated Wi-Fi environment, so you can follow along with all the lab exercises without needing special equipment. Every lab also comes with a walkthrough, so if you get stuck, you can refer to it for guidance.

VPN-Based Labs: These are deployed on Cyberwarfare Labs’ infrastructure. You just download your VPN configuration file and connect to work on labs for web application exploitation, network exploitation, and Active Directory pentesting. These labs were really enjoyable, and I appreciated that you can use any tools you’re comfortable with, not just the ones covered in the course material.
Course Materials
The course provides both video content and PDF documents that you can read offline. I genuinely enjoyed all the modules, there was always something new to learn, even with my existing experience. The OSINT and phishing modules were particularly impressive, with the instructor demonstrating some real depth of knowledge in these areas.
The exploit development module also stood out. I enjoyed it so much that I purchased two of their dedicated exploit development courses, which I’m already working through. Expect a review of those as well once I complete them.
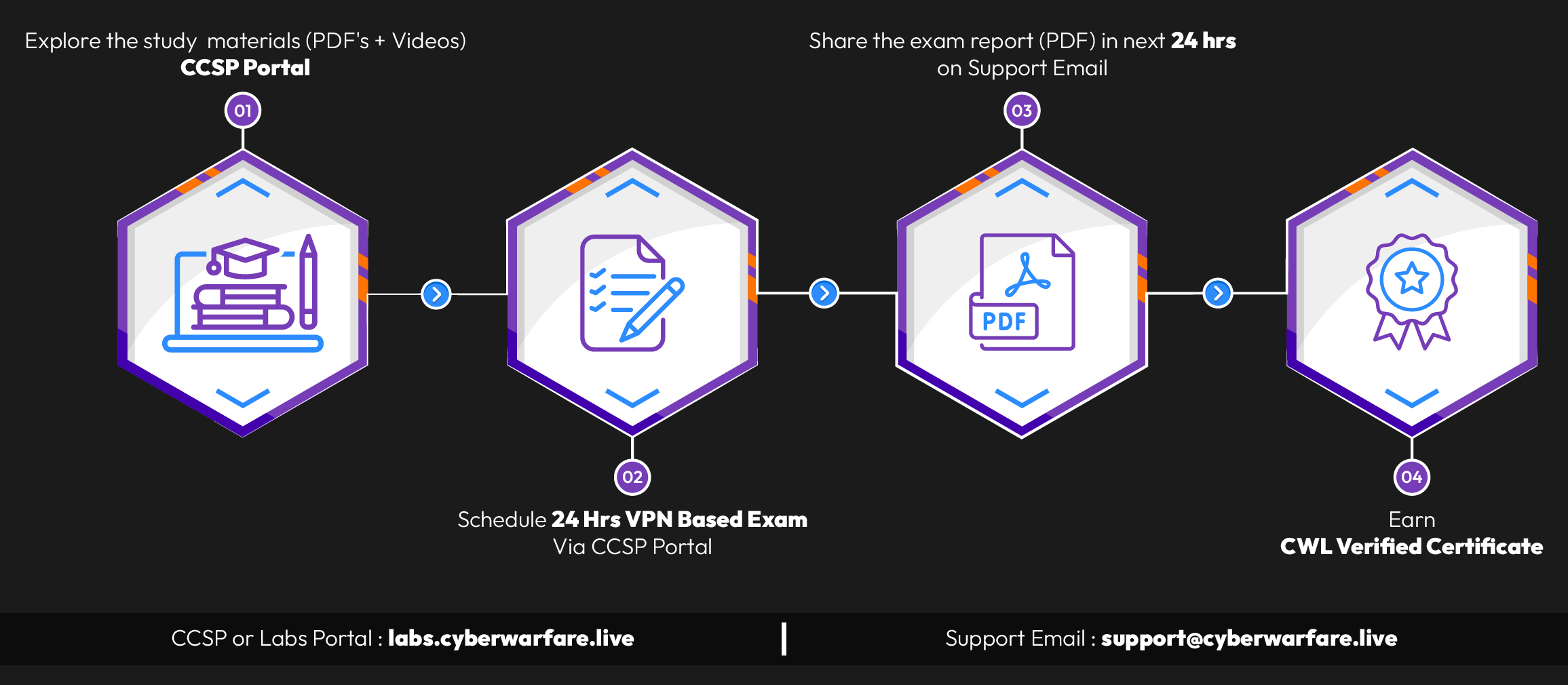
Exam Preparation
One of the best aspects of this certification is that you don’t need external resources to prepare for the exam. Everything you need to pass is covered in the 14 modules. Don’t underestimate the amount of content here, 14 modules with multiple sub-topics each adds up to a substantial amount of material.
My approach was to go through all the videos and PDFs before requesting lab access. I made detailed notes of commands and techniques covered in each module. These notes aren’t just helpful for the exam, they’re reference material you’ll use during real-world engagements and red team assessments, as the techniques taught are based on actual penetration testing methodologies.
The Exam Experience
The exam is structured like a real-world penetration test: 24 hours to complete the assessment, followed by another 24 hours to write a detailed report of your findings.
The exam lab authentically mimics an enterprise network. You perform both external and internal penetration testing, and you’re required to document everything with step-by-step reproduction instructions so the examiner can verify your findings without difficulty.
I started my exam on Saturday, November 29th, at 10:00 AM. By 5:40 PM, I had fully compromised the exam lab, a total of just under 8 hours. This was largely due to my previous experience with certifications like OSCP and CPTS. However, if you’re a beginner, don’t worry. Everything you need to succeed is covered in the course materials. If you get stuck, take a break and refer back to the study materials.
After finishing the technical portion, I took a short break and then spent 4-5 hours crafting my report. My advice: take lots of screenshots as you progress through the exam, and jot down notes in your favorite note-taking tool. This makes assembling the final report much easier. I submitted a detailed 34-page report and received my passing results four days later, faster than I expected, though they guarantee results within seven days.
Comparison with Other Certifications
In terms of exam difficulty, I’d place the CCSE between the OSCP and the PNPT.
Content-wise, the CCSE has a significant advantage over both. The inclusion of cloud pentesting, Docker container exploitation, mobile application testing, and Wi-Fi security topics not covered in the OSCP or PNPT when I took them, makes it particularly valuable for building a broad skill set.
Cost-wise, the CCSE is extremely affordable. The full price is $199, but they frequently run promotions. I purchased mine during a sale at a lower cost, and during Black Friday, they dropped the price to just $29 for a limited time. For comparison:
- OSCP: The Course & Certification Bundle (PEN-200 with 90 days of lab access and one exam attempt) costs around $1,749.
- PNPT: TCM Security’s PNPT certification with training costs $499
Given these price differences, the CCSE offers incredible value for the content you receive. However, since it doesn’t yet have the same industry recognition as the OSCP or PNPT, I’d recommend waiting for a discount or special sale to purchase it.
Final Thoughts
I highly recommend this certification to cybersecurity professionals at any level beginner, intermediate, or even seasoned professionals. There’s always something new to learn, especially at this price point. If you’re just getting started with penetration testing or want to learn about mobile, Docker, and cloud pentesting without committing to more expensive certifications, the CCSE is an excellent choice.
The combination of comprehensive content, excellent lab infrastructure, and affordable pricing makes the CCSE a valuable certification for anyone looking to broaden their penetration testing skill set. While it may not carry the same weight as an OSCP on a resume, the practical knowledge and diverse attack surface coverage make it well worth the investment especially when purchased during a promotion.