5 minutes
CDSA Review

A Clear Overview of the CDSA Certification
In this post, I’ll share my experience with the HTB Certified Defensive Security Analyst (CDSA) certification. Whether you’re new to blue teaming or already familiar with CDSA, there’s something here for everyone.
What is the HTB CDSA?

The Hack The Box Certified Defensive Security Analyst (CDSA) is a hands-on blue-team certification focused on real-world SOC operations. It evaluates your ability to monitor, investigate, detect, and respond to threats using enterprise-grade tools and realistic scenarios. The exam is fully practical and is directly based on the HTB Academy SOC Analyst role path.
Who Should Pursue It?
The CDSA is ideal for:
- Future or current SOC Analysts, DFIR analysts, and Threat Hunters
- Penetration testers or red teamers who want a defender’s perspective
- Cybersecurity learners who prefer real labs instead of theory
- Anyone who wants real experience with SIEMs, logs, and incident workflows
If you want to understand how defenders detect and respond to attacks, this certification is absolutely worth it.
Knowledge Domains Evaluated

The CDSA assesses skills across major defensive domains, all of which map directly to real SOC work:
- SOC Processes & Methodologies
- SIEM Operations (ELK / Splunk)
- Tactical Analytics
- Log Analysis
- Threat Hunting
- Active Directory Attack Analysis
- Network Traffic Analysis (incl. IDS/IPS)
- Malware Analysis
- DFIR Operations
This range makes CDSA highly complementary to offensive knowledge, giving you insight into how attacks are detected and where defenses often fail.
The HTB SOC Analyst Path (Modules & Duration)
The SOC Analyst role path contains 15 modules. Hack The Box estimates 23 days of work, but realistically it may take longer. It took me around 1.5 months to complete the entire path thoroughly.
Module List
- Incident Handling Process
- Security Monitoring & SIEM Fundamentals
- Windows Event Logs & Finding Evil
- Introduction to Threat Hunting & Hunting With Elastic
- Understanding Log Sources & Investigating with Splunk
- Windows Attacks & Defense
- Intro to Network Traffic Analysis
- Intermediate Network Traffic Analysis
- Working with IDS/IPS
- Introduction to Malware Analysis
- JavaScript Deobfuscation
- YARA & Sigma for SOC Analysts
- Introduction to Digital Forensics
- Detecting Windows Attacks with Splunk
- Security Incident Reporting
Completion of the full role path is mandatory before taking the exam. Each module combines theory with hands-on labs and real-world scenarios.
Why I Decided to Pursue a Blue-Team Certification
Coming from a pentesting/red-team background, I wanted to understand:
- How defenders detect and respond to the attacks I usually perform
- How SIEM and alert triage works at scale
- How to write better, more actionable reports
- How to identify detection gaps and strengthen defense
- The practical side of malware analysis and DFIR
CDSA opened up new perspectives especially toward malware analysis and reverse engineering and improved how I approach future offensive engagements.
Requirements Before Taking the Exam

While there are no strict prerequisites, for a smooth experience you should have:
- Basic Windows & Linux internals knowledge
- Comfort with command-line investigation
- General understanding of networking
- Familiarity with SIEM concepts
- Willingness to adopt an analyst mindset (triage → analyze → report)
The most important requirement is completing the SOC Analyst role path, which the exam is built upon.
Exam Preparation
Based on my experience, here’s what I highly recommend:
🔹 Revisit All Modules Thoroughly
Go through the modules again, including labs and exercises. The exam mirrors the Academy content closely.
🔹 Redo Skills Assessments
Repeating them helps you absorb the workflows and techniques deeply.
🔹 Master the SIEM Tools
Expect to use ELK and Splunk logs just like covered in the modules. Crafting and interpreting queries will be central.
🔹 Create a Query & Command Cheat Sheet
Include:
- SPL
- KQL
- Elastic queries
- Common forensic commands
- YARA & Sigma syntax
🔹 Review Incident Reporting Multiple Times
Blue-team reporting is detailed and process-driven. If you come from offense, this is a shift. I reviewed this module several times and read the external resources HTB recommended.
🔹 Take Many Screenshots
Everything you do in the exam should be:
- reproducible
- documented
- supported with screenshots
It will save you hours during reporting.
Exam Experience
I went all-in on this exam and genuinely had a great time.
- Start date: November 3rd
- Day 3: Reached the passing score (80 points)
- Day 4: Hit 95 points (19/20 flags)
- One task defeated me, it will haunt me forever (lol)

Use the HTB Academy search feature, it helped me quickly recall concepts when stuck.
Passing Requirements
- At least 16/20 flags
- A clean, detailed, reproducible report
Reporting
I took my time with the report because I wanted everything to be crystal clear. Good screenshots and step-by-step reasoning make the reviewer’s job easier.

Results
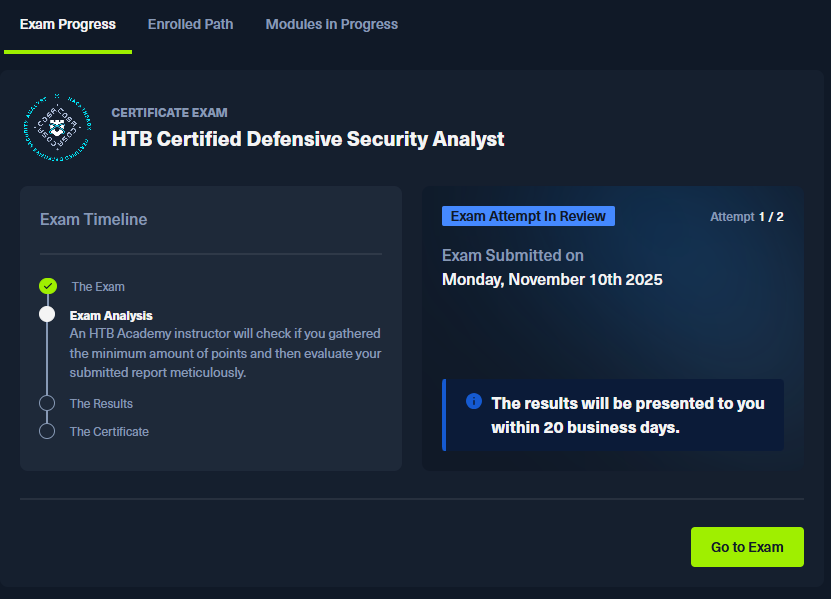
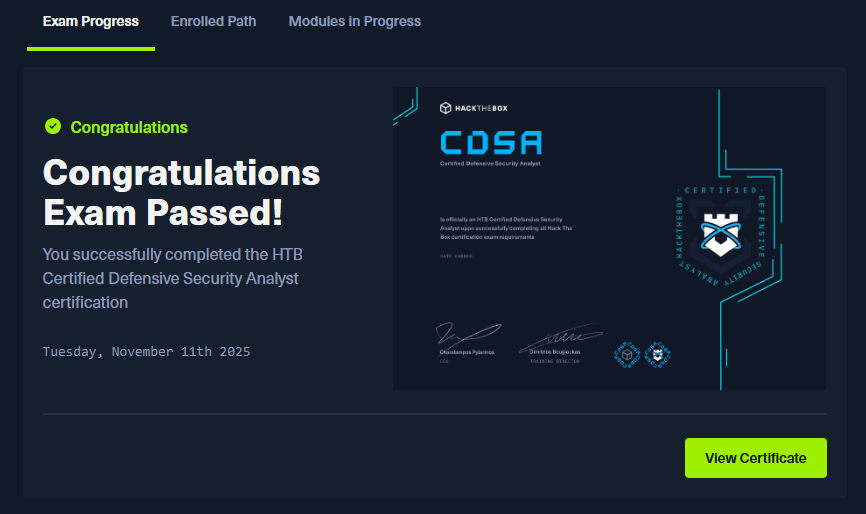
I submitted my report on November 10th. Even though results are supposed to take up to 20 business days, I got my result the next day 1 business day.Super impressive turnaround.
Recommendation
I highly recommend the CDSA to anyone wanting to:
- Break into blue teaming
- Learn SOC analysis the right way
- Strengthen detection engineering and threat hunting skills
- Gain hands-on DFIR and malware analysis exposure
- Improve their offensive thinking through defensive understanding
One of my favorite modules was Introduction to Malware Analysis, it sparked a genuine interest in Reverse Engineering and malware research, and I hope HTB adds more advanced modules in this area.
Final Thoughts

CDSA is one of the most enjoyable blue-team certifications I’ve done. It sharpened my skills, expanded my defensive mindset, and made me appreciate the amount of work SOC teams handle daily.
Whether you’re a defender or an attacker, this certification will make you better at your craft.