5 minutes
CRTP vs CRTE: Mastering Active Directory

Two years ago, I embarked on a challenging journey that would fundamentally transform my understanding of Active Directory security and red teaming. Today, I want to share my experience with two exceptional certifications from Altered Security: the Certified Red Team Professional (CRTP) and the Certified Red Team Expert (CRTE).
Why I Chose These Certifications
As someone looking to build a solid foundation in Active Directory penetration testing, I was drawn to Altered Security’s reputation for creating realistic, hands-on environments. Unlike many other certifications that rely heavily on theoretical knowledge or outdated exploitation techniques, both CRTP and CRTE focus on abusing legitimate Active Directory features and functionalities in fully patched environments.
CRTP: My First Step into Active Directory Red Teaming
The Learning Experience
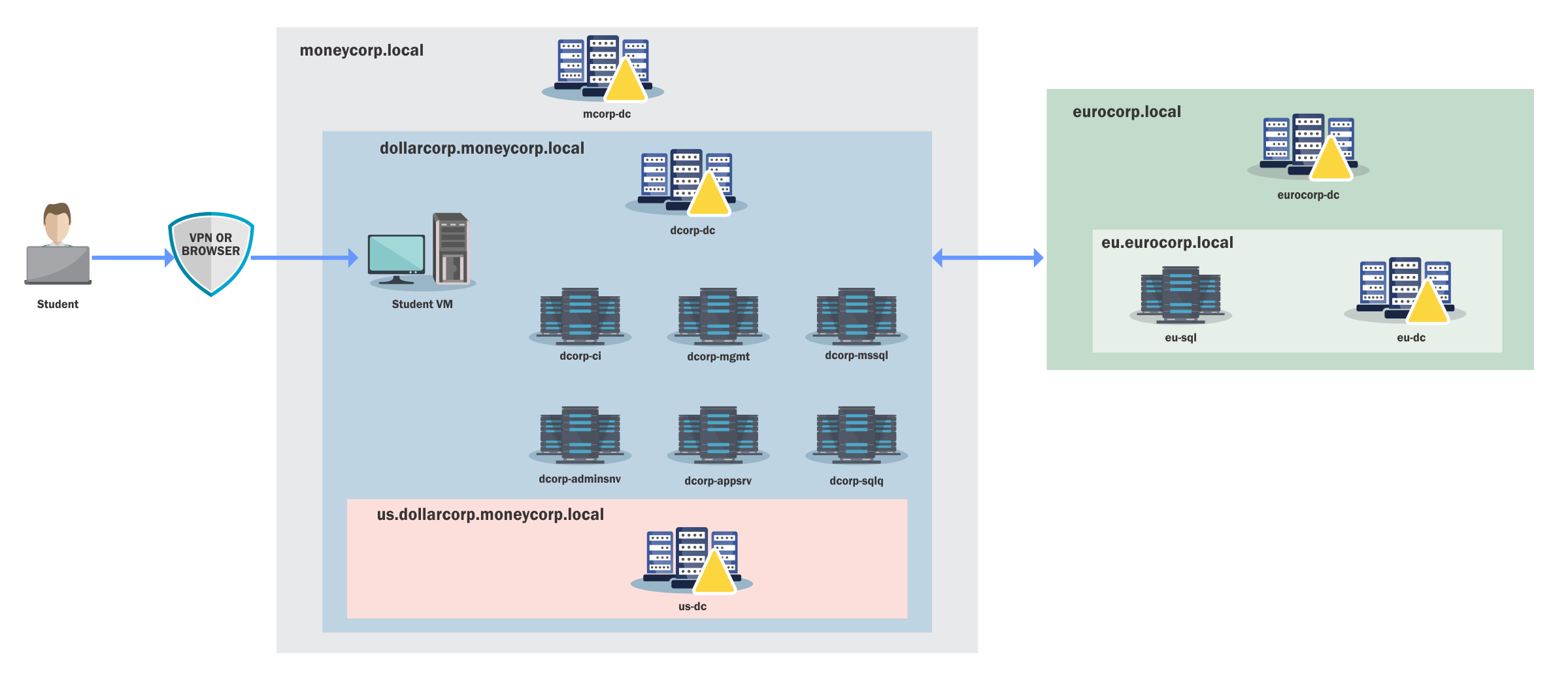
The CRTP served as my introduction to Active Directory security, covering 23 learning objectives across 59 tasks with over 120 hours of content. The course structure was comprehensive, covering everything from basic enumeration to advanced cross-trust attacks:
- Active Directory Enumeration
- Offensive PowerShell and .NET Tradecraft
- Local and Domain Privilege Escalation
- Lateral Movement Techniques
- Domain Persistence and Cross Trust Attacks
- Active Directory Certificate Services (AD CS) Abuse
The lab environment simulated a fictional financial services company with fully patched Server 2022 machines running Windows Defender, multiple forests and domains, and Server 2016 Forest Functional Level. What impressed me most was the realistic nature of the environment with minimal firewall restrictions allowed for focusing on core concepts rather than dealing with artificial barriers.
Tools and Methodology
The attack methodology followed a logical progression: Reconnaissance → Domain Enumeration → Local Privilege Escalation → Admin Reconnaissance → Lateral Movement → Domain Admin Privileges → Cross Trust Attacks → Persistence and Exfiltration.
I worked with industry-standard tools including:
- Enumeration: ActiveDirectory PowerShell Module, BloodHound, PowerView, and SharpView
- Privilege Escalation: PowerUp, PrivescCheck, and WinPEAS
- Lateral Movement: PowerShell Remoting, WinRS, Mimikatz, SafetyKatz, Impacket, and Rubeus
The Exam Challenge
The CRTP exam was intense. Starting on October 21st, I spent 16 out of the allocated 24 hours compromising the exam environment. As my first Active Directory certification, the pressure was immense, but the hands-on nature of the challenge made it incredibly engaging.
After completing the technical portion, I had another 24 hours to compile a comprehensive report. My final submission was 50 pages of meticulously detailed step-by-step instructions that would allow examiners to replicate my attacks without issues. I submitted on October 23rd and received my results on October 28th a nerve-wracking wait that ended in success.

Credential Link: Here
CRTE: Taking It to the Next Level
Advanced Concepts and Deeper Challenges
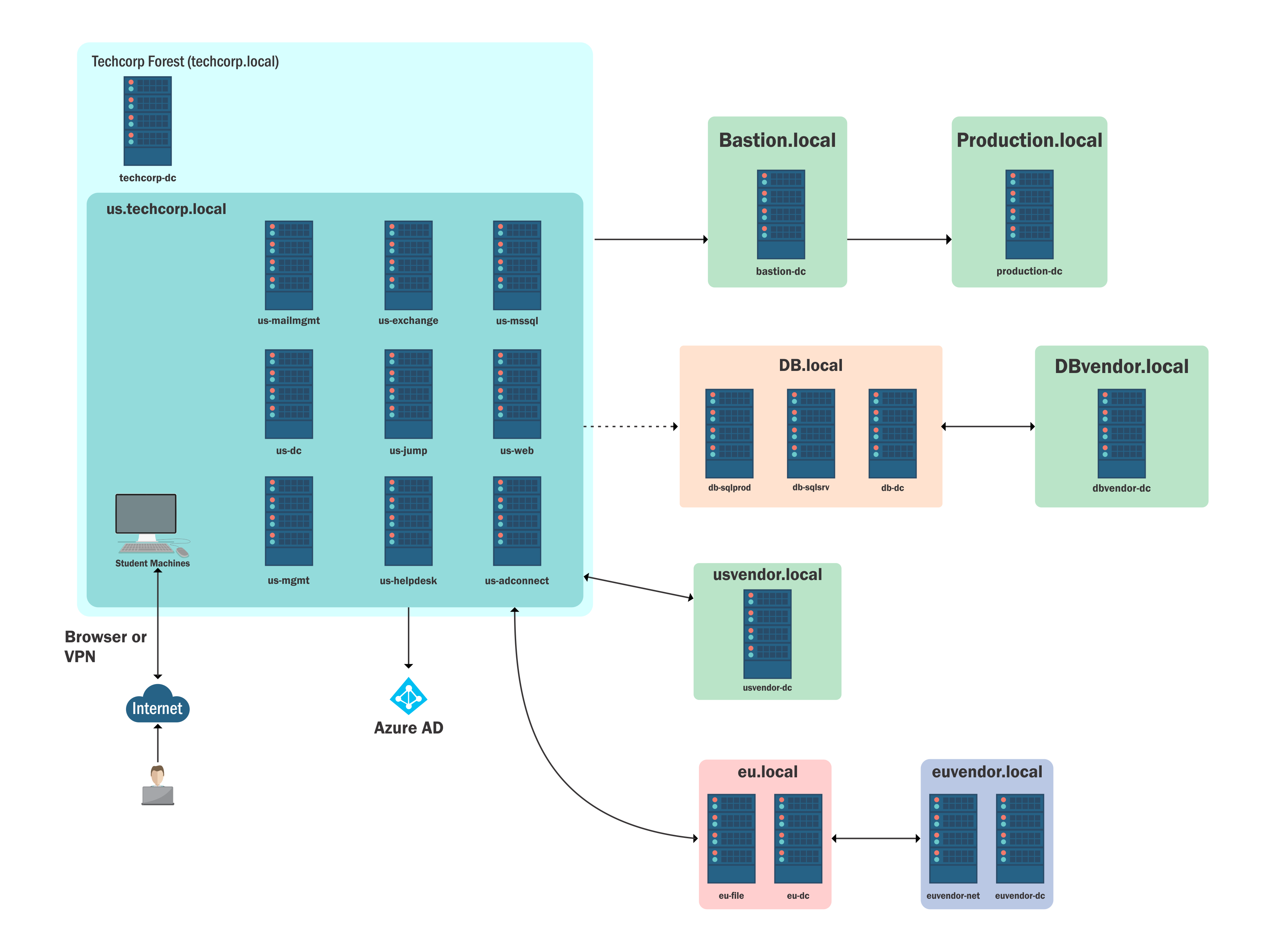
Building on the CRTP foundation, the CRTE pushed me into intermediate and expert-level territory. With 30 learning objectives across 62 tasks and over 300 hours of content, this certification demanded significantly more time and expertise.
The lab environment centered around “Techcorp,” a fictional critical technology company with segregated Active Directory forests across different departments, locations, and vendors. The environment featured almost fully patched Server 2019 machines with Server 2016 Forest Functional Level, creating a true enterprise-like challenge.
Extended Exam Experience
The CRTE exam format provided 48 hours for the hands-on portion a welcome change that allowed for more thorough exploration and rest periods. Starting on December 16th, I utilized 32 of the 48 available hours to completely compromise the exam environment.
The extended timeframe proved crucial for implementing various advanced techniques and exploring different attack vectors. After another 48-hour reporting period, I submitted my 50-page report on December 20th and received confirmation of success on December 23rd.
Credential Link: Here
The Real-World Impact
Practical Applications
The knowledge gained from both certifications proved invaluable in subsequent challenges. When I later pursued the OSCP, the Active Directory components became trivial thanks to the solid foundation these courses provided. Similarly, completing HackTheBox’s Offshore Pro Lab was significantly easier due to the advanced techniques learned through CRTE.
Career Benefits
Both certifications have established themselves as industry-recognized credentials. CRTP, in particular, has become a prerequisite for numerous job postings and is recognized by various industrial bodies and governments globally. The hands-on nature of both certifications demonstrates practical competency rather than just theoretical knowledge.
Key Takeaways and Recommendations
What Sets These Apart
- Realistic Environments: Both labs simulate actual enterprise environments with proper patching and security controls
- Feature Abuse Focus: Instead of relying on patchable exploits, these courses teach how to abuse legitimate AD functionality
- Comprehensive Support: Lab manuals, video walkthroughs, and detailed documentation provide excellent learning support
- Progressive Difficulty: CRTP builds the foundation while CRTE advances to expert-level concepts
Who Should Consider These Certifications
- Beginners looking for a solid introduction to Active Directory security (start with CRTP)
- Intermediate professionals wanting to advance their red teaming skills (CRTE)
- Anyone preparing for other certifications like OSCP or OSEP
- Security professionals working in environments with complex Active Directory implementations
Final Thoughts
Looking back two years later, I can confidently say that the CRTP and CRTE certifications were transformative experiences that significantly elevated my Active Directory security expertise. The hands-on methodology, realistic environments, and focus on feature abuse rather than exploit development provided practical skills that continue to serve me well in real-world engagements.
If you’re considering advancing your Active Directory red teaming skills, I highly recommend both certifications. The investment in time and effort pays dividends in practical knowledge and career advancement opportunities. The assume breach methodology and internal adversary perspective these courses provide are invaluable for understanding how modern Active Directory environments can be compromised and secured.
The journey was challenging, time-consuming, and occasionally frustrating, but ultimately rewarding. Two years later, the techniques and methodologies I learned continue to be relevant and applicable in today’s evolving threat landscape.