4 minutes
CRTS v2 | Part 2
CRTSv2 Certification Review – Final Thoughts After Passing the Exam
This post is the second and final part of my review of the (CRTSv2 ) certification by CyberWarFare Labs. In the first part, I covered my experience during the course. This post will wrap things up with a full breakdown of the lab, exam, preparation, and how it stacks up against similar certs.
Table of Contents
Course Material
The course is divided into two main modules:
Module 1: Initial Access
This section uses real-world case studies to demonstrate how initial access can be achieved through:
- Abusing web application vulnerabilities
- Leaked PAT (Personal Access Token) to self-hosted GitLab Runner
- Adversary-in-the-Middle (AiTM) attacks
- Manipulating Exchange Rules
- Abusing and impersonating enterprise applications like Zoom and Visual Studio
Module 2: Advanced Active Directory Attacks
Although I’ve completed both the CRTP and CRTE from Altered Security, I still learned a lot—especially about AD Certificate Services.
Topics include:
1. Kerberos Delegation
- Extensions:
- S4U2Self
- U2U
- S4U2Self + U2U
- Attacks:
- Diamond Tickets
- Sapphire Tickets
2. Linux Active Directory
- Credential Discovery
- Kerberos in Linux
- Credential Extraction
3. Group Managed Service Account (gMSA)
- Machine & User Access
4. Certificate Services
- Authentication & Abuse of ESC1, ESC4, ESC6, ESC8
- Golden Certificate Attacks
- Shadow Credentials
- Un-PAC the Hash
5. Cross-Forest Attacks
- Kerberoasting
- ACL Abuse
- Foreign Security Principal
- Trust Key Abuse
- PAM (Privileged Access Management)
- Over-Permissive Certificate Templates
Lab Experience
The lab was fun, practical, and filled with learning opportunities. You get 30 days of access via the Cyber Range portal.
Before starting the lab, you’re given access to the LMS with course PDFs and video content. Once you’re ready, you request lab access and download the OpenVPN config from the portal.
The lab mimics a Red Team engagement within an Electric PowerGrid Facility. Although the theme is OT/ICS, all attacks are IT-focused.
CRTSv2 Cyber Range
The Cyber Range includes 2 unique attack paths, both mapped to MITRE ATT&CK. There are challenge questions along the way to help track your progress.
Path 1: External to Internal Access
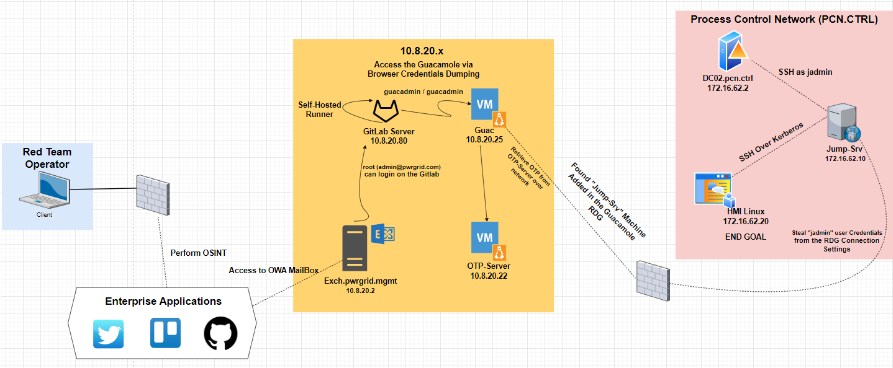
Covers a stack including:
- Exchange Servers, CI/CD Stack, MFA-Protected Apps
- Custom Web Apps & Databases, Firewall Segmentation
- Bastion Hosts, Passwordless Authentication & SSO
Path 2: Active Directory & HMI/SCADA Focus
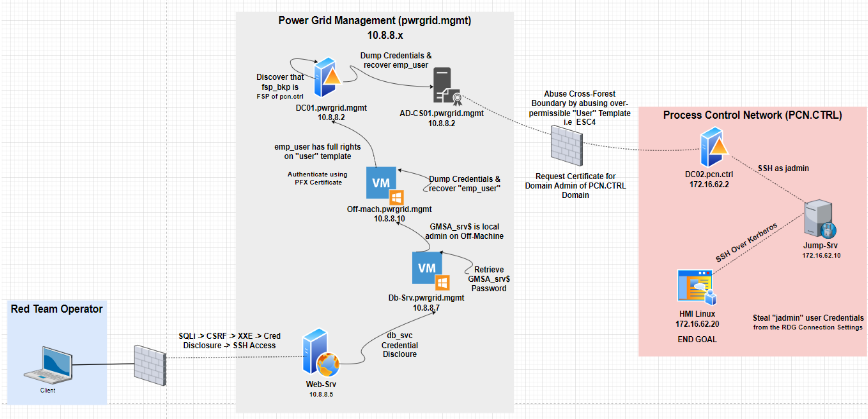
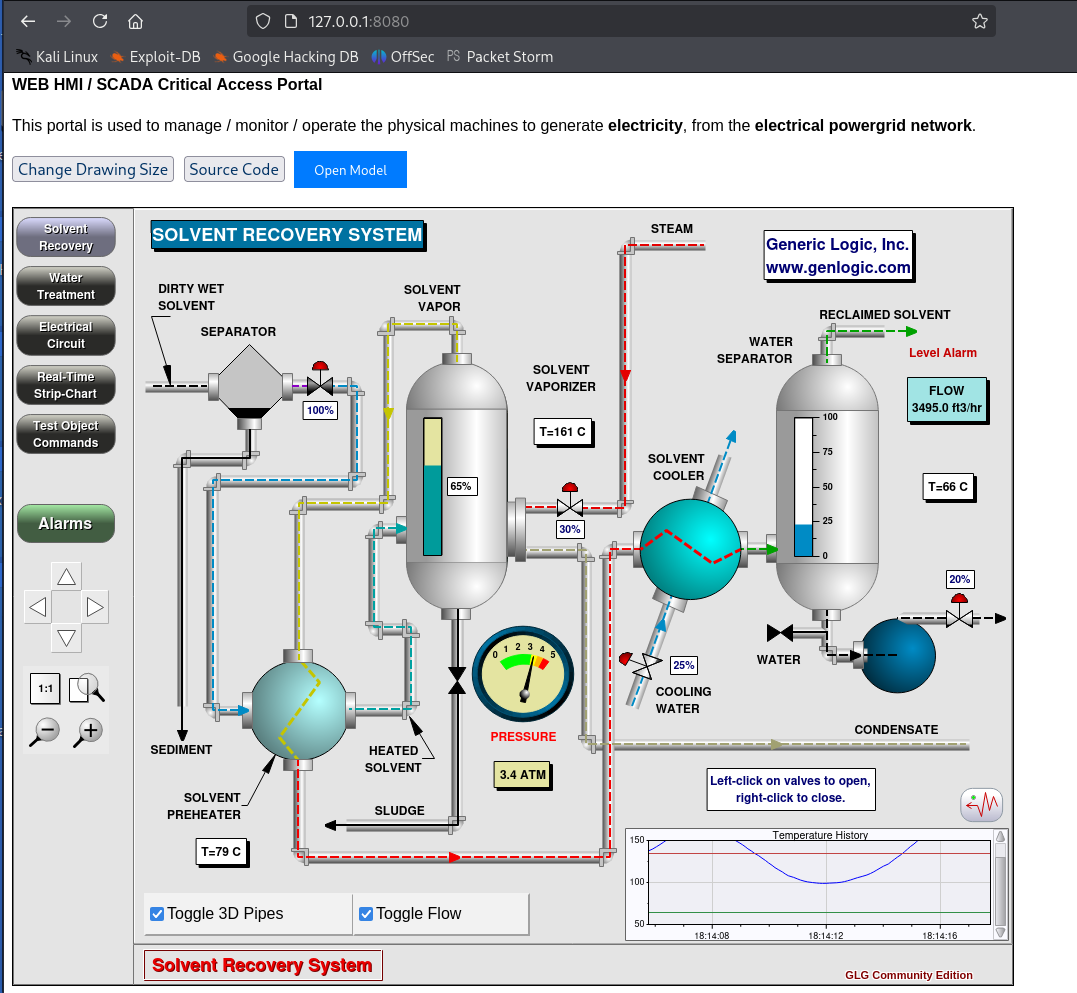
Goal: Reach the Human Machine Interface (HMI) system. Super fun and the most realistic part of the lab.
Tech stack includes:
- AD DS, CS, Managed Service Accounts
- Patched Windows & Linux Servers
- Bastion Hosts, Firewall Segmentation
- ICS Application Simulation
Exam
Cyberwarfare Labs recently launched a self-serve exam portal, and I was probably the first to book through it 😄
- Duration: 24 hours hands-on + 24 hours for report writing
- Objective: Exfiltrate a sensitive file from the target environment
- Environment: Stable – never needed to reset the lab
- Report: Not covered in the course, so prior experience is assumed
I started on March 28th at 10AM local time and completed the assessment in about 10 hours (with breaks). The exam felt very real-world focused. Chaining multiple vulnerabilities across domains, jumping between different systems, and simulating a full adversary campaign felt natural and challenging.
If you’ve done CRTP, CRTE, or CPTS (like I have), you’ll definitely feel better prepared.
Preparation
My prep strategy looked like this:
- Fully reviewed all PDFs and videos from the LMS
- Practiced every technique multiple times in the lab
- Created a personal cheat sheet on AD exploitation (soon to be shared on my GitHub)
- Reviewed HTB Academy modules on AD Enumeration & Attacks
- Read additional blog posts recommended within the course materials
Highly recommend investing time into the labs, not just to pass the exam, but to truly grasp each concept.
Comparison
Compared to other AD-heavy certs like CRTP and CRTE:
- CRTP/CRTE = assume-breach style (internal access from the start)
- CRTSv2 = full cyber kill chain, from external to internal compromise
CRTSv2 stands out for its realistic adversary simulation, requiring you to leverage multiple attack vectors from initial access to domain dominance.
Final Thoughts
Highly recommended. 💯
- Great price point (especially when discounts are available)
- Labs are realistic, immersive, and educational
- The exam feels like a real Red Team engagement
- Targeted at intermediate/advanced professionals in offensive security
If you’re just getting started, I’d suggest beginning with something like CRTA to get your AD fundamentals in place.
If you’re into Red Teaming and AD exploitation, CRTSv2 should definitely be on your radar. I’ve gained a ton from this course and will absolutely apply it in real-world assessments.
If you have any questions, feel free to reach out or connect with me on (LinkedIn ) or (Twitter ).
Stay sharp.
763 Words
2025-04-14 17:48